How to Activate and Deactivate Users
How to Activate Users#
When do the Users get activated?#
When an admin activate the user:#
An admin activates a user when the user's account is ready for access to the platform, typically after verifying that the registration details are correct and the user meets any required criteria. Activation may occur once the admin has reviewed the account, assigned appropriate roles or permissions, and ensured that the user is authorized to access the system or perform specific tasks within platforms like ZeuZ. This process helps maintain security and control over user access.
Effects of Activation:#
Activation of a user account has the following effects:
- Access to the Platform: The user gains full access to the system or platform features.
- Role Assignment: The user can assume roles and permissions assigned by the admin, enabling them to perform tasks or access specific modules.
- Collaboration: The user can now collaborate with other team members, participate in projects, and contribute to tasks or tests.
- Notification and Alerts: The user may start receiving relevant notifications, updates, or alerts based on their activities and roles.
- Tracking and Reporting: The user's actions and contributions can be tracked within the system, allowing for reporting and accountability.
Activation ensures that users can fully engage with the system while adhering to defined roles and security protocols.
Steps#
- From the Menu bar, go to the Admin then List option.
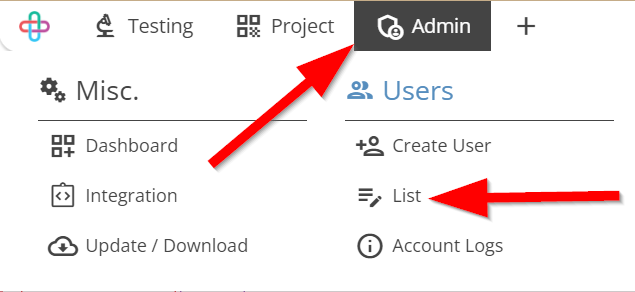
- Go to the Users page.
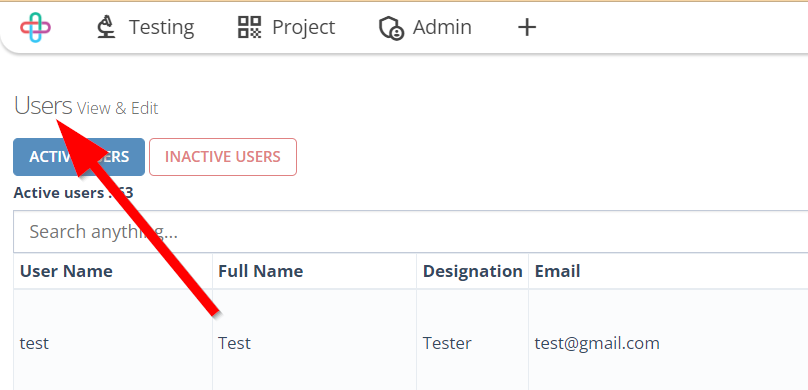
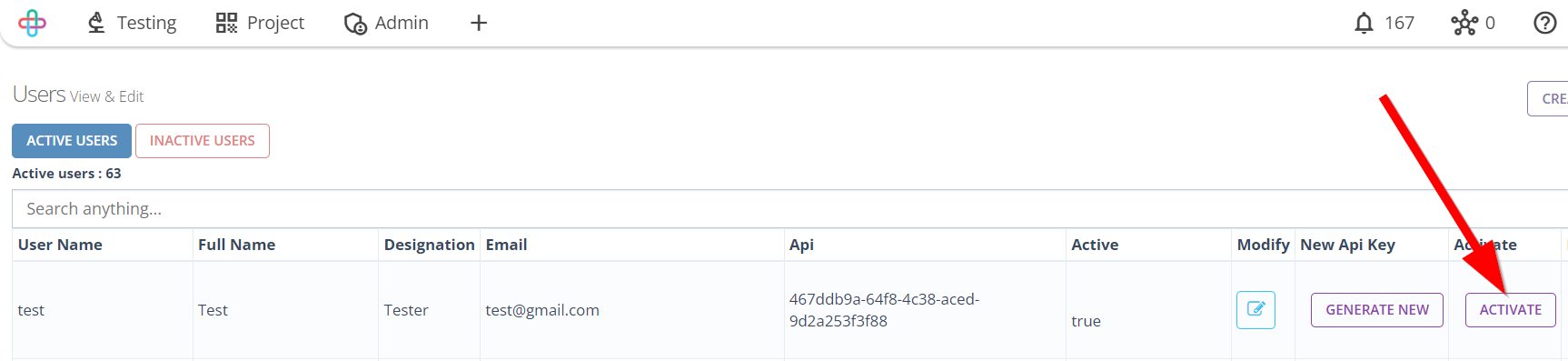
- Click on the Activate button of the required User.
The Activate button is used to enable or activate a specific user account in software testing, allowing them access to the system.
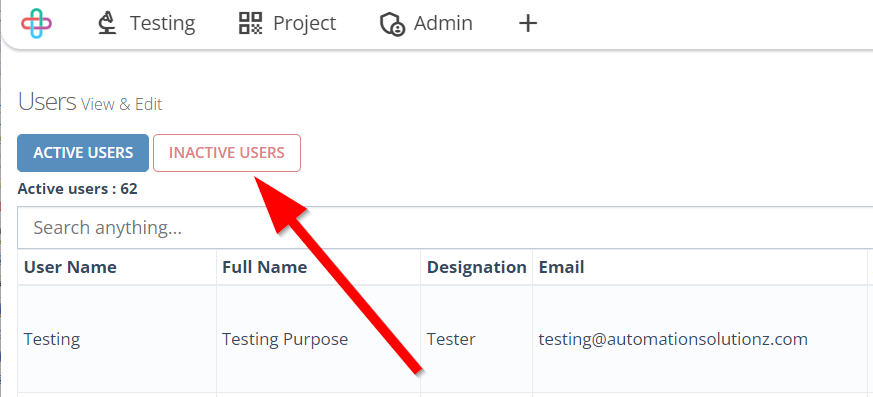
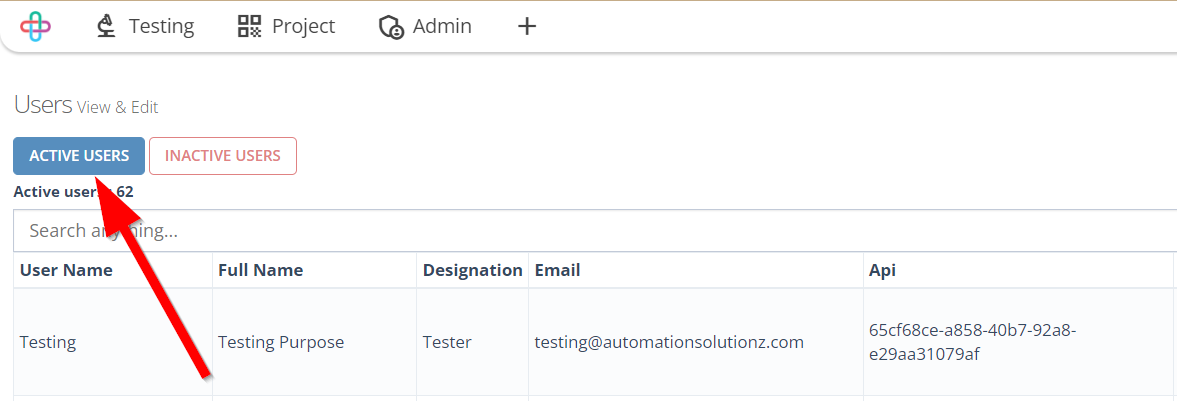
- To see Activated users, click on the Active Users button.
The Active Users button is used to display a list of users who currently have active or enabled accounts in the system.
How to Deactivate Users#
When do the Users get deactivated?#
When an admin deactivate the user:#
Deactivating a User, often performed by an admin, involves the suspension or revocation of a user's access and privileges within a system or platform. This action is taken for various reasons, including employee departures, policy violations, or security concerns. The process typically includes disabling login capabilities, removing access permissions, locking or freezing accounts, and revoking special privileges or services. User deactivation helps maintain security and control over system access.
When a user attempts to enter their password more than five times:#
When a User attempts to enter their password more than five times, it typically triggers a security measure. After multiple unsuccessful login attempts, the system may lock the user account temporarily to prevent unauthorized access. This is a common security practice to safeguard against brute force attacks or unauthorized login attempts. The exact number of allowed login attempts and the duration of the lockout can vary depending on system settings and security policies. Users may need to contact an administrator or follow a password recovery process to regain access to their account after such a lockout.
Effects of Deactivation:#
Deactivation has various effects depending on the context. It usually involves the suspension or disabling of a user, device, software, account, or service. For instance,
- When a user is deactivated, they lose access to a system or platform.
- Devices can be deactivated if reported as lost or stolen, rendering them inoperable.
- Some software licenses allow for deactivation on one device so that the software can be deactivated on another. Deactivation in this sense releases a license for use elsewhere.
- Account deactivation on online platforms results in the loss of access or content removal for violating terms.
Additionally, Deactivation can extend to security features and services, potentially increasing vulnerability or causing service interruptions. The specific consequences of deactivation depend on the circumstances and established policies, typically serving as a security measure to prevent unauthorized access or misuse.
Steps#
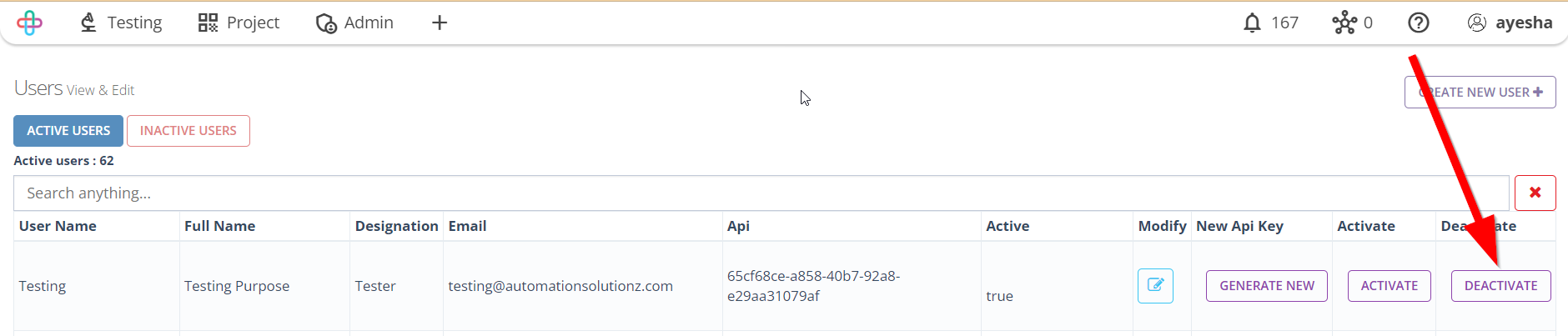
- To Deactivate a user, click on the Deactivate button of the required user.
The Deactivate button is used to disable or turn off a user's access or account, typically when they are no longer active or authorized to use the software system.
- To see Deactivated users, click on the Inactive users button.
Inactive users typically refer to users who have been deactivated or disabled, meaning their access to the system has been restricted or removed. This is often done to ensure security and prevent unauthorized use of the software.